Do you rely on a security plugin to protect your WordPress site? Are you confident about what most of the features in these plugins actually do?
Personally, I’m not a big fan of using security plugins. Instead, I’ve spent time learning and implementing effective strategies to safeguard my WordPress sites without relying on them.
Here are my top recommendations to keep your WordPress site secure.
Create a Strong Username and Password for your Site
The first step is using a password manager, so you can create and use long and complex passwords.
I use Bitwarden to save all my passwords but feel free to use the password manager you like the most.
Password Managers have options to create complex passwords.
You can create a complex username and password for your WordPress site.
| #1 | ZKA4UkfoAESmcUUuCcv3@g%Tm%Dk |
| #2 | dw6PL3Wxt@i2cvnC$vhYNo997@GSNU |
That would make your username and password almost impossible for hackers and bots to crack using brute force attacks.
According to Bitwarden’s Password Strength Testing Tool, the username and the password shown above will take centuries to crack.
If a brute force attack works on your site is because you are way too ignorant or dumb to manage a website.
Block XML-RPC Access
The XML-RPC protocol allows multiple login attempts in a single request, so this means attackers can submit numerous login attempts in one go, bypassing standard rate-limiting measures that protect the login page.
If your site doesn’t use XML-RPC, consider disabling it altogether. This can be done using a PHP snippet.
add_filter('xmlrpc_enabled', '__return_false');Also, you can create a mu-plugin and forget about those types of attacks once and for all.
<?php
/**
* Plugin Name: Disable XML-RPC
* Description: Disables XML-RPC functionality in WordPress.
* Author: TicoLibre
* Version: 1.0
*/
// Disable XML-RPC
add_filter('xmlrpc_enabled', '__return_false');WordPress Core, Plugins and Themes
There are several things that you can do to make your site doesn’t get hacked via your theme and plugins.
- Install and Keep the plugins that you really need.
- Update all plugins as soon as there is an update or wait a few days only if you are completely sure that your site them and plugins don’t have an active vulnerability.
- Keep your version of WordPress updated.
- Download plugins and themes directly from the developers and WordPress.org
- Don’t install nulled plugins.
- Use mu-plugins instead of regular plugins.
Try to follow WordPress Security blogs and subscribe to their mailing lists to get news about the themes and plugins with active vulnerabilities.
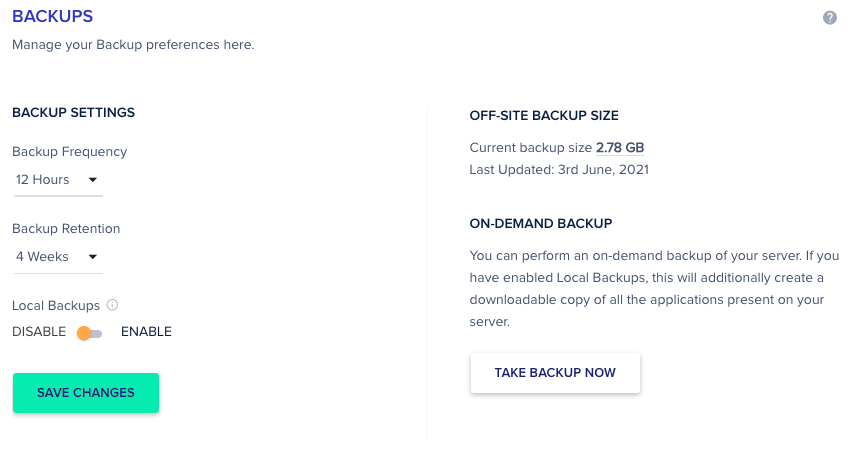
Make Site Backups Regularly
Make sure that you use a hosting provider or Cloud Hosting panel that backs up your site regularly.
Cloudways does this for me. You can retain those backups for four weeks.
The frequency of the backups could be set to a minimum of one hour.
Besides that, I recommend:
- Using All in One WP Migration to make backups that you can save in a Dropbox or Google Drive account.
- Making copies of the database more regularly.
You need to be ready to restore your site in case something bad happens to one of your sites.
Cleaning a site can be expensive.
Restoring from a backup can save you lots of time and money.
Don’t save backups in your WordPress installation. Those could be downloaded and used to access your database and hack your WordPress site.
Protect your Database, FTP and SSH Access
There are many hosting providers and cloud hosting panels that will do something to prevent your WordPress sites get hacked.
The Cloudways panel has the option to protect your Database, SFTP, and SSH.
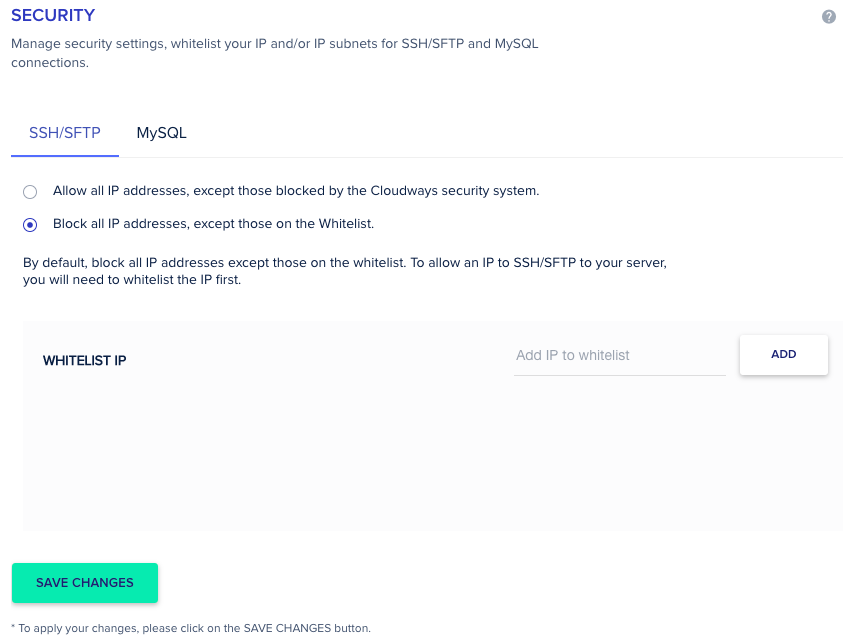
If I don’t add your IP address, you won’t be able to access my database, check my WordPress Installation via FTP or access my server and run remote commands.
Create a Firewall
The last thing that you can do to ensure that your site is super safe is to create Cloudflare Firewall Rules.
You can create up to five rules to help you deal with most types of threats.
I am a bit more proactive with WordPress security, but this will be more than enough to make sure that nobody can check for PHP files on your WordPress installationewew.
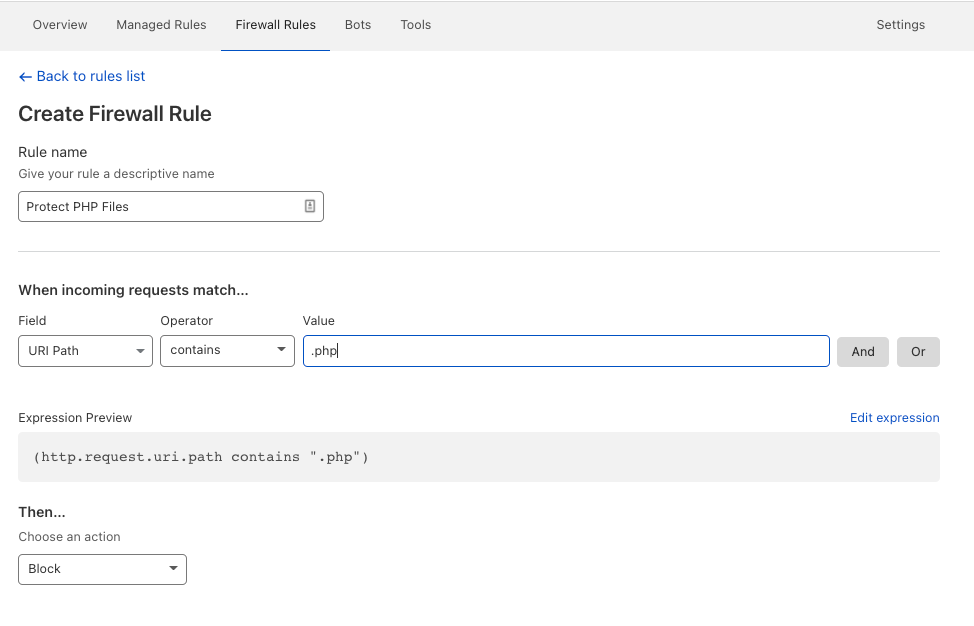
Whitelist your IP address and your server IP address to make sure you don’t get blocked by the rules you create.
Lock Down the wp-content Folder
Many attacks against WordPress are automated and assume files are stored in the default location.
WP-Content contains your images, videos, documents but also:
themes/ → your active and inactive themes
plugins/ → installed plugins
mu-plugins/ → must-use plugins
So one thing you could do is move files that are meant to be public to another location and create a Firewall rule to lock down wp-content.
This is how you do it.
To be able to do that successfully, you need to be aware of all the stylesheets and scripts added by plugins and themes.
Nothing to worry about if you are using mu-plugins or a custom theme cause you have full control over that.
Conclusion
I recommend using security plugins when users don’t know sh*t about how basic WordPress security works or if users are too busy to learn about how to keep most threats at bay.