Are you thinking about blocking or challenging autonomous system numbers with CloudFlare?
ASNs are used to identify and organize groups of networks on the internet.
Some examples of well-known companies or organizations that have been assigned ASNs include:
- Google (AS15169)
- Amazon Web Services (AS16509)
- Facebook (AS32934)
- Akamai Technologies (AS20940)
By blocking or challenging certain ASNs, organizations can restrict access to known sources of malicious traffic, such as botnets.
A botnet is a network of compromised computers or devices that are controlled by a central authority, typically a cybercriminal or a group of hackers.
In this post, we will discuss the reasons why you may or may not choose to block ASNs and the process for doing so.
Should I Block or Challenge ASNs?
If you use CloudFlare, you will find that you can challenge, whitelist or block internet companies or hosting providers.
I don’t think that blocking or challenging traffic coming from an specific hosting or internet company is a good investment of your time.
To give you some perspective
The number of unique autonomous networks in the routing system of the Internet surpassed 5,000 in 1999, reached 30,000 by late 2008, grew to 35,000 by mid-2010, and 42,000 by late 2012. By mid-2016, the count had risen to 54,000, and it reached 60,000 in early 2018. As of March 2021, the number of allocated Autonomous System Numbers (ASNs) exceeded 100,000
Autonomous System (Internet)
Based on that I think it is a ridiculous idea to pretend that you are going to create a set of effective rules based on autonomous system numbers .
What difference would blocking 20 companies make?
I don’t know the internet well enough to make decisions about what ASN to Block or what to challenge.
You should focus on protecting your site at the path level or query string level instead.
To Block or To Challenge an ASN
Let’s say that you still want to do something at the ASN Level
I don’t usually recommend blocking ASN numbers because if you don’t do it right, you might end up blocking real users or some legitimate services you are currently using.
Even when an ASN has a lot of bot activity like this one, I choose to challenge its traffic.
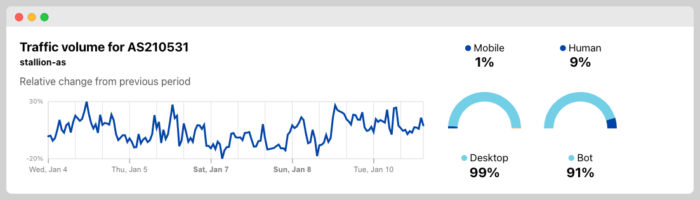
Challenging ASNs has never been my number #1 Firewall and now it is not even something I consider.
How to Block ASN with CloudFlare Firewall Rules
Blocking or challenging traffic coming from different hosting providers or internet companies is quite easy using CloudFlare.
- You can name the firewall rule any name you want
- Choose AS Num from the field options
- Choose “equals” from the operator options
- Add the “ASN Number” in the value field
- Choose “or”
- Add another “ASN Number”
- Repeat the process if you need to
- Choose an action.
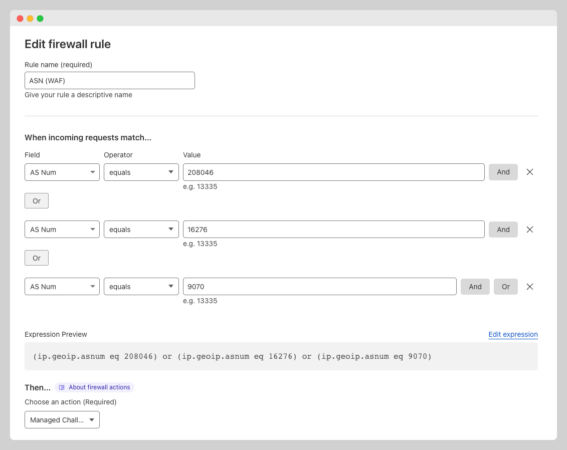
I suggest using the managed challenge unless you are 100% sure that traffic from an ASN is full of bots, scrapers, and other bad actors.
If you want to leave some space to challenge other types of behavior, you can use this approach instead in which you add several ASNs in one field.
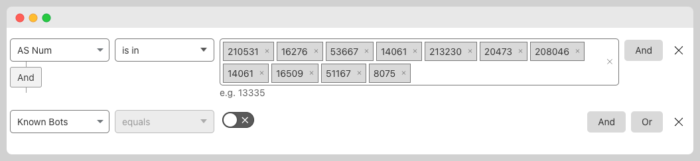
I suggest adding the “known bots” options if you want to challenge ASNs like Microsoft but you don’t want to block Microsoft Bing user agent.
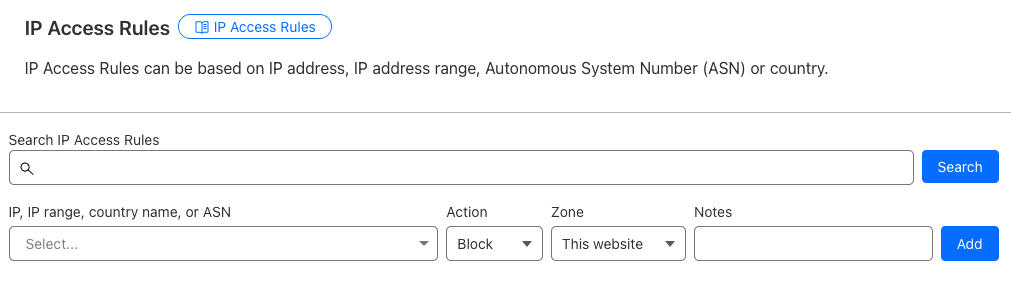
Alternative Method to Block ASNs
For those who want to save one of the precious rules, remember that you can go to WAF and then tools to block or challenge Autonomous System.
What I don’t like about using this method is that you can see logs to determine if CloudFlare is blocking legitimate users or services.
What ASN Numbers to Block?
I recommend creating firewall rules to block sensitive areas of your site.
Then check the logs and see the most common hosting providers or internet companies used to attack your site.
At the moment of writing this post, I noticed lots of attacks coming from Cloud Asset so this ASN could be challenged from now on.
Cloudflare has important stats on the percentage of bot activity coming from ASNs
You can check that by visiting Cloudflare Radar
You can also rely on lists created by a third-party website such as the one provided by SpamHouse
List of Worst ASNs
These are some of the worst ASNs based on my Cloudflare logs with stats taken from Cloudflare Radar
Keep in mind that bot activity doesn’t mean malicious bot activity.
| ASN | Company | Bot | Human |
| 208046 | Hotslick | 97% | 3% |
| 210531 | STALLION | 91% | 9% |
| 16509 | AMAZON | 91% | 9% |
| 16276 | OVH | 70% | 30% |
| 14061 | Digital Ocean | 84% | 16% |
| 213230 | Hetzner | 83% | 17% |
| 212441 | CloudAssets | 94% | 6% |
| 20473 | AS Choopa | 75% | 25% |
| 43624 | PQ Hosting | 70% | 30% |
| 8075 | MICROSOFT-CORP | 93% | 7% |
| ASN | Company | Bot | Human |
| 52000 | MIRhosting | 71% | 29% |
| 35624 | SILVERSTAR | 73% | 27% |
| 24940 | HETZNER | 95% | 5% |
| 31898 | ORACLE-BMC | 81% | 19% |
| 19318 | IS-AS-1 | 93% | 7% |
| 211138 | PRIVATEHOSTING | 95% | 5% |
| 198375 | INU | 99% | 1% |
| 32748 | STEADFAST | 73% | 27% |
| 44546 | ALFATELECOM | 89% | 11% |
| 55286 | SERVER-MANIA | 72% | 28% |
| ASN | Company | Bot | Human |
| 197207 | MCCI-AS | 77% | 23% |
| 58224 | TCI | 89% | 11% |
| 44244 | IRANCELL-AS | 83% | 17% |
| 43754 | ASIATECH | 93% | 7% |
| 50810 | MOBINNET | 92% | 8% |
| 36352 | COLOCROSSING | 74% | 26% |
| 45102 | ALIBABA | 95% | 5% |
Filing an Abuse Report
If you do wanna do some good for the World, you can report the IP to the hosting provider so they take action.
I wouldn’t bother filing a report when the attacks come from sh*tty hosting providers
I recently reported a Google Cloud IP that was scanning for exploits and vulnerabilities.
It got blocked like two hundred times in two minutes so I concluded that they really wanted to be reported.
Hopefully, reputable companies do something about it.
Blocking an ASN: Final Thoughts
If Blocking ASNs is something you want to do, that rule must complement other firewall rules, since hackers, bots, and attackers can rotate the hosting providers they use.
Also, remember to check the logs from time to time and see if real visitors or services are getting blocked by the rule.
For example:
- If you are using an ad network such as Ezoic, blocking or challenging Amazon servers would be a terrible idea.
- If you are optimizing your site’s SEO using Ahrefs Webmaster Tools, you should exclude OVH from your Firewall rules.
- Not all ASNs refer to hosting providers, some of them are Internet Service Providers (ISPs) and for obvious reasons, it is not recommended to block them.
- If you make money using display ads, you will find that there are lots of advertising companies bots crawling your site on a daily basis.



